Token Ring (IEEE 802.5)
Token Ring was developed by IBM in the 1970s and is described in the IEEE 802.5 specification. It is no longer widely used in LANs. Token passing is the method of medium access, with only one token allowed to exist on the network at any one time. Network devices must acquire the token to transmit data, and may only transmit a single frame before releasing the token to the next station on the ring. When a station has data to transmit, it acquires the token at the earliest opportunity, marks it as busy, and attaches the data and control information to the token to create a data frame, which is then transmitted to the next station on the ring. The frame will be relayed around the ring until it reaches the destination station, which reads the data, marks the frame as having been read, and sends it on around the ring. When the sender receives the acknowledged data frame, it generates a new token, marks it as being available for use, and sends it to the next station. In this way, each of the other stations on the ring will get an opportunity to transmit data (even if they don't have any data to transmit!).
Token Ring networks provide a priority system that allows administrators to designate specific stations as having a higher priority than others, allowing those stations to use the network more frequently by setting the priority level of the token so that only stations with the same priority or higher can use the token (or reserve the token for future use). Stations that raise a token's priority must reinstate the priority level previously in force once they have used the token. In a Token Ring network, one station is arbitrarily selected to be the active monitor. The active monitor acts as a source of timing information for other stations, and performs various maintenance functions, such as generating a new token as and when required, or preventing rogue data frames from endlessly circulating around the ring. All of the stations on the ring have a role to play in managing the network, however. Any station that detects a serious problem will generate a beacon frame that alerts other stations to the fault condition, prompting them to carry out diagnostic activities and attempt to re-configure the network.
Frame format
Two basic frame types are used - tokens, and data/command frames. The token is three bytes long and consists of a start delimiter, an access control byte, and an end delimiter. The format of the token is shown below.

The Token Ring token
A data/command frame has the same fields as the token, plus several additional fields. The format of the data/command frame is shown below.
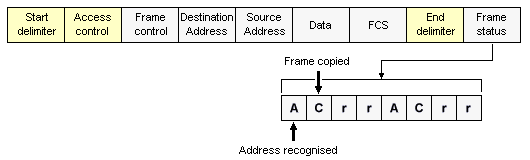
The Token Ring frame format
- Start delimiter - alerts each station of the arrival of a token or frame.
- Access control byte - contains the priority field, the reservation field, the token bit and a monitor bit.
- Frame control byte - indicates whether the frame contains data or control information. In a control frame, this byte specifies the type of control information carried.
- Destination and source addresses - two six-byte fields that identify the destination and source station MAC addresses.
- Data - the maximum length is limited by the ring token holding time, which defines the maximum time a station can hold the token
- Frame check sequence (FCS) - filled by the source station with a calculated value dependent on the frame contents. The destination station recalculates the value to determine whether the frame was damaged in transit. If so, the frame is discarded.
- End delimiter - signals the end of the token or frame, and contains bits that may be used to indicate a damaged frame, and to identify the last frame in a logical sequence.
- Frame status - a one-byte field that terminates a frame, and includes the one-bit address-recognized and frame-copied fields. These one-bit fields, if set, provide confirmation that the frame has been delivered to the source address and the data read. Both fields are duplicated within the frame status byte.
If the network is quiet and none of the stations has any data to transmit, the token simply circulates around the ring continuously. When a station has data to transmit, it waits until it receives the token, marks it as "busy" by setting the token bit, adds the data and/or control information to create a data or command frame, and transmits the frame to the next station. Each station that receives the frame will re-transmit the frame to the next staion until it reaches the destination station. This station reads the data, sets the address recognised and frame copied bits in the frame status field, and transmits the frame to the next node. When the frame arrives back at its point of origin, the originating station generates a new token, which it transmits to the next station, even if it has further data to send. In this way, each station network has an equal number of opportunities to transmit data. Because only one token is allowed to exist on the network, only one station can transmit at any one time, and collisions cannot occur. Although the IEEE 802.5 specification reflects IBM's Token Ring technology, the specifications differ slightly. IBM specifies a star topology, with all end stations star-wired to a multi-station access unit (MSAU), wheras IEEE 802.5 does not specify a topology (although virtually all IEEE 802.5 implementations were based on a star). In addition, IEEE 802.5 does not specify a media type, while IBM originally specified shielded twisted pair cable. The table below summarises the IBM and IEEE 802.5 specifications.
| IBM Token Ring | IEEE 802.5 | |
|---|---|---|
| Data rate | 4 or 16 Mbps | 4 or 16 Mbps |
| Stations per segment | STP - 260 UTP - 72 | 250 |
| Topology | Star | Not specified |
| Media | Twisted pair | Not specified |
| Signalling | Baseband | Baseband |
| Access method | Token passing | Token passing |
| Encoding | Differential Manchester | Differential Manchester |
Priority System
Token Ring networks provide a user-configurable priority system that allows stations that are designated as having a high-priority to use the network more frequently. Token Ring frames have two fields that control priority - the priority field, and the reservation field. Only stations with a priority equal to, or higher than, the value contained in a token's priority field can aquire the token. Once the token is in use, only stations with a priority value higher than that of the transmitting station can reserve the token for the next pass around the network. When the next token is generated, it is set to the priority of the reserving station. Any station that raises the token's priority level must restore it to the previous level after use.
Fault Management
One station (it can be any station on the network) is selected to be the active monitor. The active monitor acts as a central source of timing information for the other stations on the network, and performs various maintenance functions, including making sure that there is always a token available on the network. The active monitor also sets the monitor bit on any data or command frame it encounters on the ring so that, in the event that a sending device fails after transmitting a frame, the frame can be prevented from circling the ring endlessly and thereby denying access to the network for other stations. If the active monitor receives a frame with the monitor bit already set, it removes the frame from the ring and generates a new token.
The use of a multi station access unit (or wiring center) in a star topology contributes to network reliability, since these devices can be configured to check for problems and remove faulty stations from the ring if necessary. A Token Ring algorithm called beaconingcan be used to detect certain types of network fault. When a station detects a serious problem on the network (a cable break, for example), it transmits a beacon frame which initiates an auto-reconfiguration process. Stations that receive a beacon frame perform diagnostic procedures and attempt to reconfigure the network around the failed areas. Much of this reconfiguration process can be handled internally by the MSAU. The MSAU contains relays that switch a computer into the ring when it is turned on, or out of the ring when the computer is powered off. A MSAU has a number of ports to which network devices can be connected, a ring-out port allowing the unit to be connected to another MSAU, and a ring-in port that can accept an incoming connection from another MSAU. A number of MSAUs can thus be connected together in daisy-chain fashion to create a larger network. The ring-out port of the last MSAU in the chain must be connected back to the ring-in port of the first MSAU.
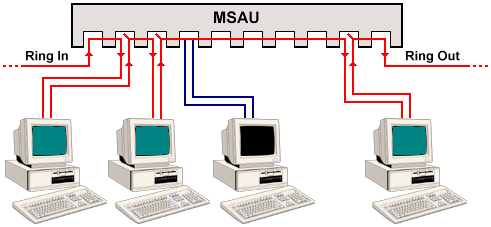
Connections in a multi-station access unit
